-
Why I Cancelled ChatGPT Plus: Saving €15/Month with Gemini Advanced

The Switch: Why I Dumped ChatGPT Plus for Gemini For a long time, I was a loyal subscriber to ChatGPT Plus. I happily paid the €23.99/month to access the best AI models. But recently, my focus shifted. I’m currently optimizing my finances to invest more in index ETFs and aim for early retirement (FIRE). Every Euro counts.…
-
Forget Google: Build Your Own Search API with SearXNG

Learn how to self-host SearXNG on Proxmox or Docker, use its free search API, and integrate it with Node-RED for OSINT, automation, and privacy.
-
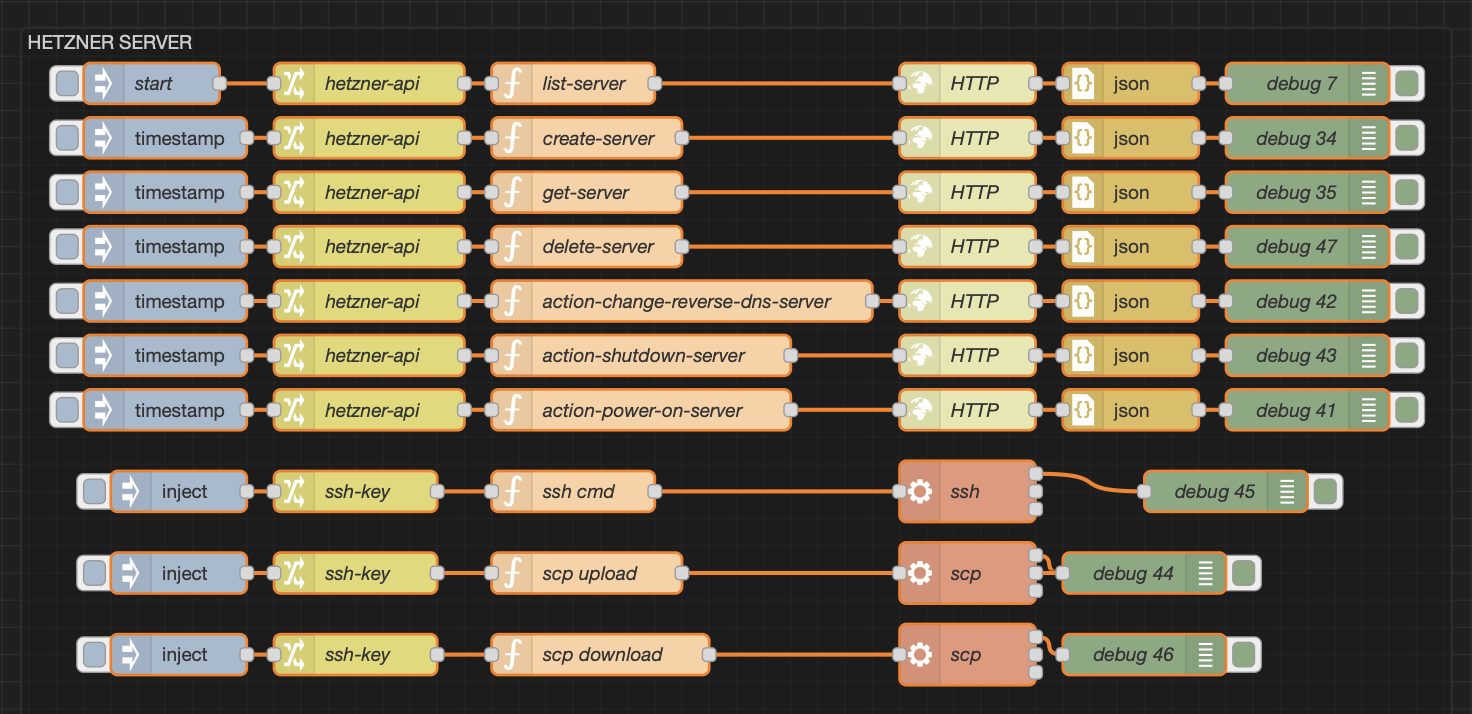
How to Orchestrate Hetzner Cloud Servers with Node-RED Flows

Learn how to automate Hetzner Cloud with Node-RED. This guide shows step-by-step flows for creating, managing, and destroying cloud workers on demand. You’ll see how to use Change and Function nodes, handle API calls, check server status, run tools like Masscan or Nmap remotely, and even manage reverse DNS and A-records with Cloudflare. Perfect for…
-
ClamAV on Steroids: 35,000 YARA Rules and a Lot of Attitude

Built a scalable ClamAV + 35K YARA rule cluster with FastAPI, HAProxy, and DB storage for fast, insightful malware analysis – born out of frustration.
-
I Tested a Viral Anti-Spam Prompt. It Failed Spectacularly

Okay, I’ll admit it, I was rage-baited into writing this article. Lately, I’ve been spending some time automating all of my LinkedIn tasks. I don’t actually like LinkedIn, but I do want to build a large network. So what’s a guy to do? Obviously, connect ChatGPT to LinkedIn. Now, let’s be clear: this is a…
-
Caffeine & Exploits: Hacking Coffee Machines with Social Engineering

How I hacked dozens of WMF coffee machines using social engineering, default PINs, and a bit of boldness. A fun real-world red teaming story—from free coffee to security awareness.
-
From Krakow with Access: A Casual Hotel Tablet Hack

Disclaimer: The information provided on this blog is for educational purposes only. The use of hacking tools discussed here is at your own risk. For the full disclaimer, please click here. A while ago, I got invited by a large corporation to visit their offices in Krakow. I got lucky since all the hotels were full,…
-
Outsmarting Enterprise Email Security: The Easy Way

Disclaimer: The information provided on this blog is for educational purposes only. The use of hacking tools discussed here is at your own risk. For the full disclaimer, please click here. Like most enterprises—or any business, really—you probably have multiple email security appliances. Sometimes these are part of your provider package like in Google Workspace. Typically,…
-
Forget ChatGPT, I Built My Own Local AI with AMD RX 7900 XTX, Ollama & DeepSeek-R1

The journey to bringing you this guide was paved with rage and hardship. Before we go any further, let me be clear: local AI is nowhere near as good as ChatGPT or similar online tools. Without solid prompt engineering, you’ll mostly get weird, useless responses. That said, DeepSeek-R1 (32B) is hands down the best local…
-
From Typos to Treason: The Dangerous Fun of Government Domain Squatting

Hey there 👋 Since you’re reading this, chances are you’ve got some chaos brewing in your brain. I love it. For legal reasons I must kindly ask you to read and actually understand my disclaimer. Disclaimer: The information provided on this blog is for educational purposes only. The use of hacking tools discussed here is…