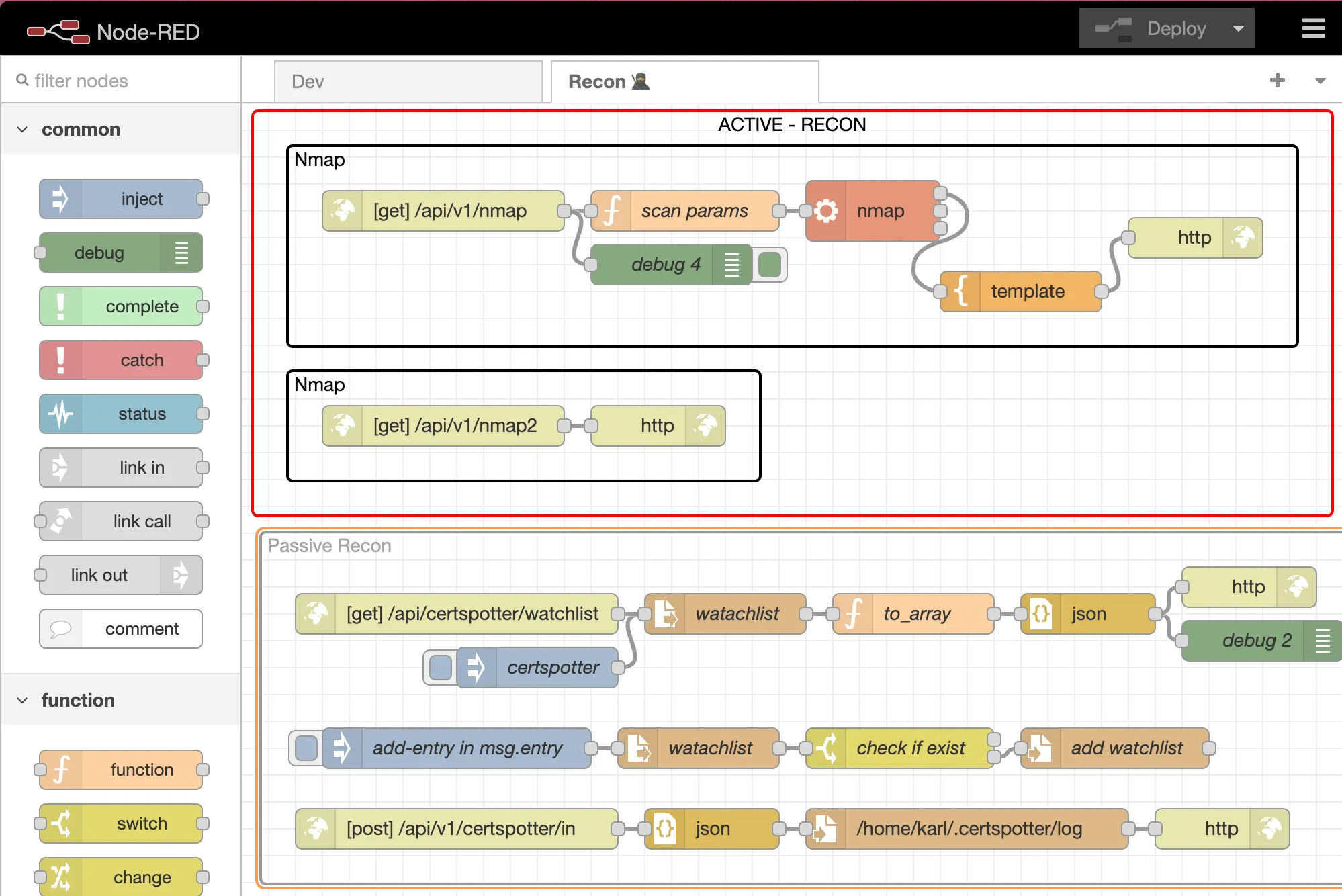
Node-RED, building Nmap as a Service
Introduction In the realm of cybersecurity, automation is not just a convenience but a necessity. Having a tool that can effortlessly construct endpoints and interconnect various security tools can revolutionize your workflow. Today, I’m excited to introduce you to Node-RED, a powerhouse for such tasks. This is part of a series of hacking tools automated with…
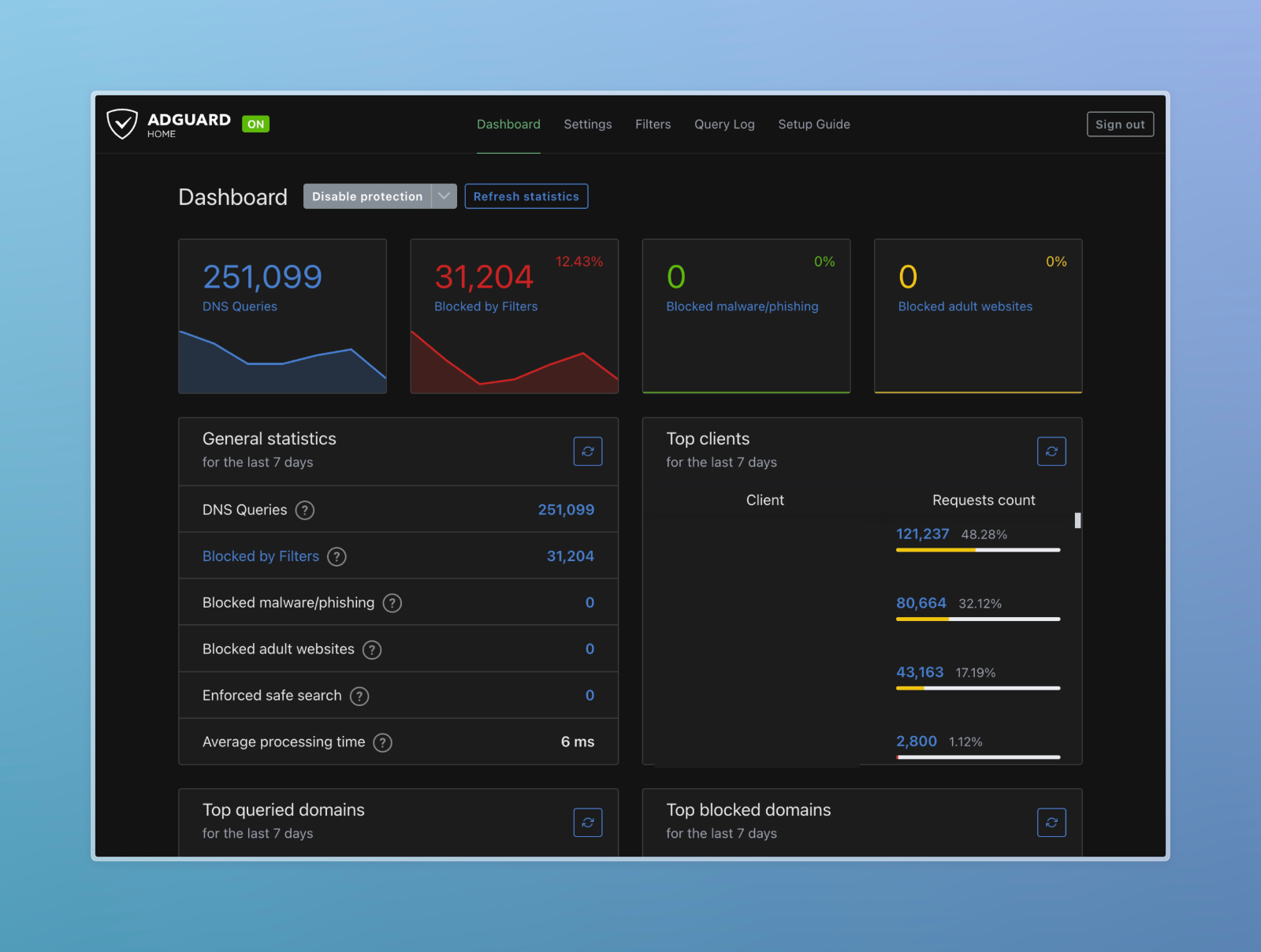
AdGuard Home for security and blocking ads
Introduction In today’s digital age, the internet is saturated with advertisements and trackers, leading to slower browsing speeds and potential security threats. To combat these issues, leveraging AdGuard Home as a central ad blocker provides several key benefits, such as improved security and faster internet speeds. While browser plugins like “uBlock Origin” offer protection for…
Unveiling HTML and SVG Smuggling
Disclaimer: The information provided on this blog is for educational purposes only. The use of hacking tools discussed here is at your own risk. For the full disclaimer, please click here. Introduction Welcome to the world of cybersecurity, where adversaries are always one step ahead, cooking up new ways to slip past our defenses. One technique…
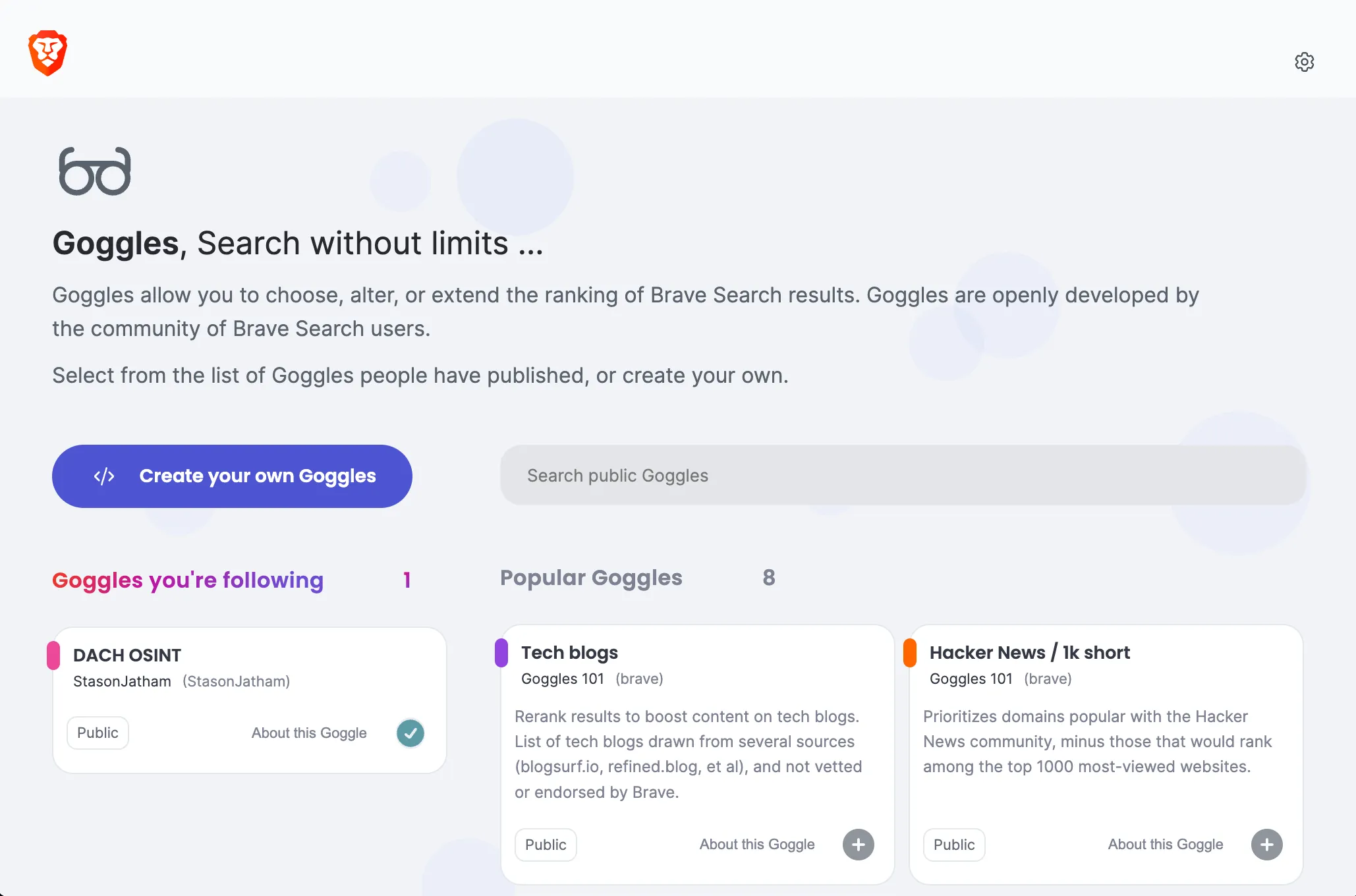
Using Brave Search Goggles for Recon
Introduction The world’s most potent OSINT (Open Source Intelligence) tools are search engines. They collect, index, and aggregate all the freely available information on the internet, essentially encapsulating the world’s knowledge. Nowadays, the ability to enter a topic in a search bar and receive results within milliseconds is often taken for granted. Personally, I’ve developed a profound…
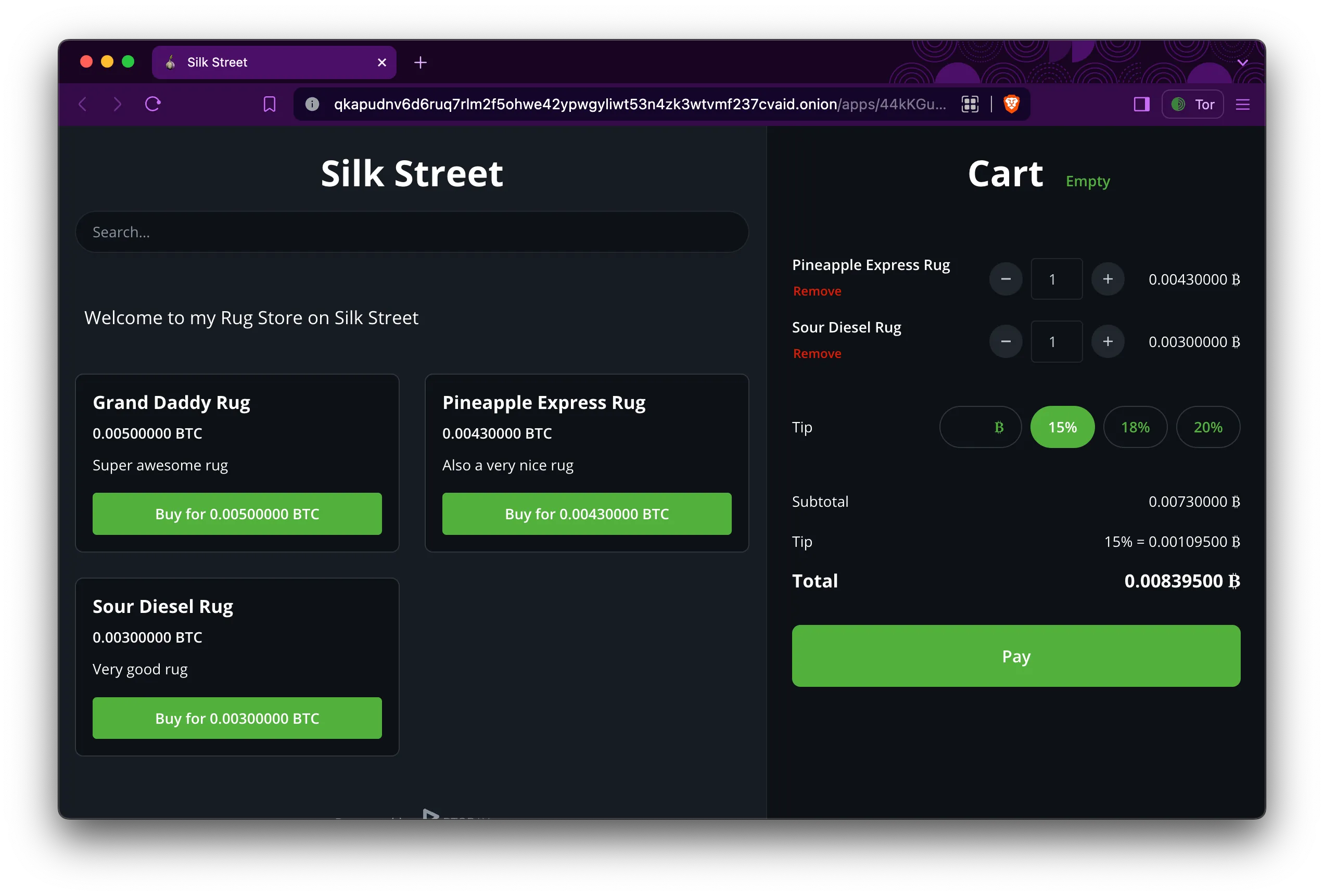
How to sell rugs online (fast) – hosting your own Dark web market
Disclaimer: The information provided on this blog is for educational purposes only. The use of hacking tools discussed here is at your own risk. For the full disclaimer, please click here. Welcome to the Dark Web Rug Emporium! So, you’ve made the bold decision to take your rug-selling business to the mysterious realms of the internet’s…
Vaultwarden: A Lightweight, Self-Hosted Password Manager
What is Vaultwarden ? According to their GitHub page: If you’re unfamiliar with Vaultwarden or Bitwarden, here’s a quick primer: Vaultwarden is a self-hosted password manager that allows you to securely access your credentials via web browsers, mobile apps, or desktop clients. Unlike traditional cloud-based solutions, Vaultwarden is designed for those of us who value control over our…
Unlock the Power of Remote Development with code-server
In the fast-paced world of software development, flexibility and efficiency are paramount. Enter code-server, an innovative tool that allows you to run Visual Studio Code (VS Code) in your browser, bringing a seamless and consistent development environment to any device, anywhere. Whether you’re working on a powerful desktop, a modest laptop, or even a tablet (pls don’t!), code-server…
How to Get Real Trusted SSL Certificates with ACME-DNS in Nginx Proxy Manager
Today, I’m going to show you how you can obtain real, trusted SSL certificates for your home network or even a public website. Using this method, you can achieve secure HTTPS for your web services with certificates that browsers recognize as valid. Fun fact: the very website you’re reading this on uses this same method!…
Denial-of-Wallet Attacks: Exploiting Serverless
Disclaimer: The information provided on this blog is for educational purposes only. The use of hacking tools discussed here is at your own risk. For the full disclaimer, please click here. Introduction In the fast-paced world of cyber warfare, attackers are always on the hunt for new ways to hit where it hurts – both in…
Building a static site search with Pagefind
Today, I’m here to spill the beans on a magical tool that’ll have you searching through your static site like a pro without sacrificing your users’ data to the digital overlords. Say goodbye to the snooping eyes of Algolia and Google, and say hello to Pagefind – the hero we need in the wild world of web…